Environmental Monitoring for Marine Energy Sites
Key Parameters and Monitoring Techniques

Performance Metrics
Evaluating essential performance indicators (KPIs) plays a pivotal role in assessing system health and uncovering potential problems. These measurements offer valuable insights into system functionality across multiple tiers, ranging from single components to the entire system framework. Observing metrics such as response durations, error frequencies, and resource usage enables proactive detection of performance constraints and areas for improvement. Mastering these indicators proves indispensable for sustaining peak system efficiency and delivering satisfactory user interactions.
Critical performance measurements might encompass processor usage, memory allocation, network bandwidth, and disk operations. Continuous surveillance of these metrics facilitates early identification of unusual patterns or deviations. Analyzing these data trends helps forecast potential complications and implement preventive strategies.
Resource Allocation and Management
Strategic distribution of system resources remains fundamental for ensuring consistent operation and performance. Appropriate handling of processing power, memory capacity, and storage space guarantees that applications receive adequate resources for optimal functioning. Imbalanced resource distribution – whether excessive or insufficient – can result in reduced performance, instability, and potential system failures. Recognizing the correlation between resource assignment and application requirements forms the foundation for superior system operation.
Effective resource management employs various methodologies including automated scaling mechanisms, resource limitations, and sophisticated workload distribution techniques. These approaches ensure efficient utilization of available resources to meet fluctuating system demands. Proper resource allocation plays a crucial role in preventing system strain and maintaining reliable service quality.
Monitoring Tools and Technologies
Selecting appropriate monitoring solutions is critical for accurate performance tracking and system oversight. The market offers diverse options, ranging from community-developed tools to comprehensive commercial platforms. The selection process should consider system-specific requirements, financial constraints, and technical capabilities. Choosing the optimal monitoring solution significantly impacts the ability to detect and resolve problems efficiently.
Contemporary monitoring platforms frequently incorporate intuitive interfaces and graphical representations that enable immediate observation and evaluation of critical performance metrics. These analytical capabilities empower system administrators to quickly address developing issues and sustain optimal performance levels. Advanced systems often integrate notification features, alerting administrators about urgent problems to ensure rapid response times.
Security and Compliance
Security considerations remain paramount in system oversight practices. Continuous surveillance of security incidents and system logs proves essential for threat detection and response. Maintaining rigorous security protocols is fundamental for safeguarding confidential information and system integrity. Implementation of comprehensive protective measures, including intrusion prevention systems and network barriers, proves crucial for deterring unauthorized access and data compromises. Regular security assessments and vulnerability testing are necessary for identifying and addressing potential weaknesses.
Alignment with industry regulations and standards represents another vital component of system monitoring. Monitoring procedures and tools must conform to applicable legal requirements, ensuring proper handling and storage of sensitive information. Compliance with regulatory frameworks is imperative for avoiding legal consequences and preserving stakeholder confidence.
Alerting and Response Mechanisms
Efficient notification systems are indispensable for immediate identification and resolution of critical incidents. Alert protocols provide timely warnings about potential problems, enabling administrators to implement corrective measures promptly. These systems should effectively prioritize alerts based on severity, ensuring that administrators concentrate on the most pressing matters. This proactive methodology reduces operational interruptions and maintains system reliability.
Effective incident response procedures are equally significant. Clearly defined protocols for addressing alerts and system issues are essential for efficient problem resolution. Establishing a systematic response strategy lessens incident impact and accelerates recovery processes. Thorough documentation of incident responses proves valuable for learning from past experiences and enhancing future performance.
Long-Term Monitoring and Data Management
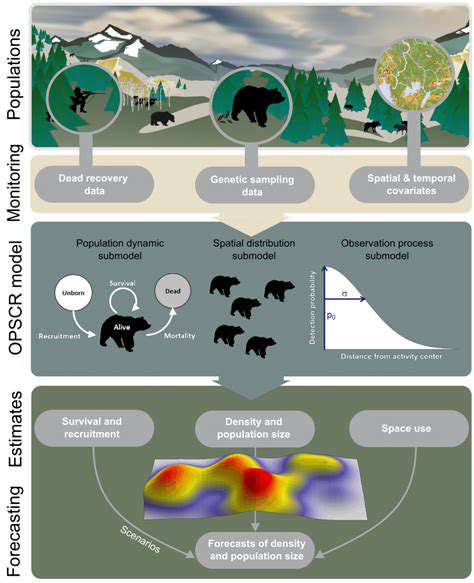
Long-Term Data Collection Strategies
Successful extended monitoring initiatives demand meticulous preparation and consideration of multiple variables, including available resources, study objectives, and environmental conditions. A comprehensive data gathering framework is crucial for maintaining information accuracy and uniformity throughout the monitoring period. This framework should explicitly define collection methodologies, timing, locations, as well as procedures for data recording and preservation.
Developing resilient data handling infrastructure is essential for the sustained effectiveness of monitoring projects. This encompasses creating protected and retrievable storage solutions for original data, supplementary information, and analyzed results. Information must remain easily accessible for examination, reporting, and subsequent investigations, guaranteeing that valuable collected data remains available for future use.
Data Management Systems
Choosing suitable data organization platforms is fundamental for preserving the reliability and availability of long-term monitoring information. These platforms should accommodate substantial datasets, support various file formats, and permit straightforward data access and interpretation. Web-based storage solutions offer expandable capacity and remote access capabilities for researchers and partners in different locations.
Data verification and quality assurance processes are necessary to maintain the precision and dependability of collected information. Implementing defined criteria and validation procedures helps detect and rectify potential inaccuracies or discrepancies in the gathered data.
Data Security and Accessibility
Protecting the confidentiality and availability of extended monitoring data is critical to prevent unauthorized entry, information loss, and maintain data accuracy. Deploying strong protective measures, including user permissions and data encryption, is essential for securing sensitive monitoring information.
Data Analysis and Reporting
Regular examination of accumulated data is necessary to detect developments, correlations, and modifications over time. This analytical process can influence operational decisions, direct preservation activities, and enhance understanding of the monitored environments.
Thorough documentation of findings is vital for conveying long-term monitoring results to diverse audiences. These reports should present information clearly and comprehensibly for various interested parties, including scientists, government officials, and community members.
Data Visualization and Interpretation
Graphical representation methods can effectively convey complex data relationships and trends to different audience types. Selecting suitable visualization approaches enables clear and concise data presentation, facilitating easier comprehension and analysis of monitoring outcomes.
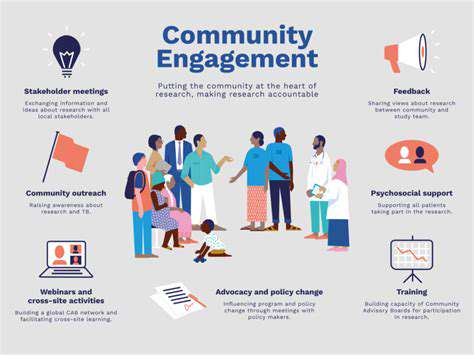
Collaboration and Knowledge Sharing
Cooperative initiatives among researchers, stakeholders, and decision-makers are crucial for optimizing the value of extended monitoring data. Encouraging information exchange and results dissemination through academic papers, training sessions, and professional gatherings will ensure broader utilization of the collected knowledge. Strategic communication methods are important for increasing awareness and participation in monitoring programs.