Cybersecurity for Renewable Energy Infrastructure: National Security Implications
Protecting Critical Infrastructure: A National Security Imperative
Cybersecurity for essential services extends beyond operational concerns to become a matter of national importance. The interconnected nature of modern society means that disruptions to power distribution, water treatment, or transportation networks can have catastrophic consequences for public welfare and economic stability. Implementing comprehensive security measures represents a fundamental requirement for ensuring the continuous operation of these vital systems.
The Escalating Threat Landscape
Cyber threats continue evolving in sophistication and scale, with adversaries employing increasingly complex attack methods. Critical infrastructure represents an attractive target for various malicious actors, whether motivated by financial gain, political objectives, or ideological reasons. This dynamic threat environment demands security strategies that can adapt rapidly to emerging risks and attack vectors.
Vulnerabilities in Essential Systems
Many critical infrastructure components rely on aging technology with inherent security limitations. These legacy systems often operate with obsolete software and insufficient protection mechanisms, creating vulnerabilities that attackers actively exploit. Addressing these weaknesses requires systematic modernization efforts combined with implementation of contemporary security controls and continuous staff education.
The Role of Collaboration and Information Sharing
Effective infrastructure protection requires coordination among government entities, private sector operators, and security specialists. Establishing mechanisms for rapid threat intelligence exchange proves essential for timely identification and response to emerging cybersecurity challenges. Standardized communication protocols and response frameworks enhance the speed and effectiveness of coordinated defensive actions.
The Importance of Workforce Training and Awareness
Human factors contribute significantly to security vulnerabilities across critical infrastructure sectors. Comprehensive training programs that teach personnel to recognize phishing attempts, suspicious behavior, and potential security threats form a crucial component of organizational defenses. Fostering a culture of security awareness among all employees helps establish multiple layers of protection against potential breaches.
Implementing Advanced Security Technologies
Modern security solutions including next-generation firewalls, behavior-based threat detection systems, and comprehensive endpoint protection platforms provide essential tools for infrastructure defense. Properly integrating these technologies into a unified security architecture significantly enhances an organization's ability to detect and neutralize threats. Continuous system monitoring and proactive threat analysis enable early identification of potential security incidents.
International Cooperation and Standards
Cybersecurity threats represent a global challenge that transcends national boundaries. Developing international security standards and facilitating cross-border cooperation helps create consistent protection measures across jurisdictions. Sharing technical expertise, threat data, and best practices among nations strengthens collective defenses against increasingly sophisticated cyber threats targeting critical infrastructure worldwide.
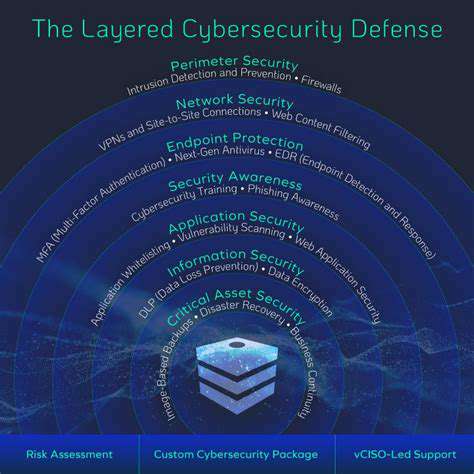
Mitigating Risks: A Multi-Layered Security Strategy
Identifying Potential Threats
The foundation of effective risk management begins with comprehensive threat identification. This process requires meticulous examination of all system components, operational processes, and external factors that could introduce vulnerabilities. A thorough evaluation must consider both technical weaknesses and human factors, including potential insider threats and social engineering risks. Neglecting this critical first step can leave organizations exposed to preventable security incidents.
By systematically analyzing various threat scenarios, organizations can develop proactive mitigation strategies that address risks before they materialize. This forward-looking approach to risk management helps maintain operational stability and supports long-term organizational objectives despite evolving security challenges.
Implementing Robust Controls
Following threat identification, organizations must establish appropriate security controls tailored to their specific risk profile. These protective measures should range from basic preventative actions to sophisticated technical safeguards. Control implementation requires balancing security needs with operational requirements, ensuring that protections remain effective without creating unnecessary barriers to productivity.
Essential security controls typically include strict access management protocols, comprehensive data encryption methods, and continuous system monitoring solutions. Regular evaluation and testing of these controls ensures they remain effective against emerging threats while maintaining alignment with organizational needs and industry standards.
Developing Contingency Plans
Despite robust preventive measures, security incidents remain possible, making comprehensive contingency planning essential. These response plans should outline specific actions for various potential scenarios, including data compromises, system failures, and natural disasters. Well-structured contingency plans enable rapid, coordinated responses that minimize operational disruption and facilitate efficient recovery processes.
Effective contingency planning requires considering impacts on personnel, operational continuity, and financial resources. Regular testing and updating of these plans ensures they remain relevant as organizational needs and threat landscapes evolve. Such preparations prove invaluable when responding to actual security incidents.
Prioritizing Resources Effectively
Strategic resource allocation represents a critical component of successful risk management. Organizations must evaluate potential threats based on their likelihood and potential impact to determine appropriate resource distribution. Focusing resources on high-priority risks ensures maximum protection where most needed, while maintaining efficient use of available security investments.
This prioritization process should guide decisions regarding security technology acquisitions, staff training initiatives, and process improvements. Aligning resource allocation with identified risks helps create a balanced security posture that protects critical assets without unnecessary expenditure.
Monitoring and Evaluating Performance
Effective risk management requires continuous oversight and assessment of security measures. Regular monitoring helps identify control weaknesses, emerging threats, and changing risk profiles. Comprehensive evaluation processes should incorporate technical assessments, operational reviews, and feedback from all relevant stakeholders to ensure complete understanding of security effectiveness.
This ongoing evaluation cycle enables organizations to adapt their security strategies in response to new information and changing circumstances. Continuous improvement processes help maintain strong security postures despite evolving threats and business requirements.
Communicating and Collaborating
Successful risk management depends on clear communication and cooperation across all organizational levels. This includes transparent sharing of risk assessments, security policies, and incident response procedures with relevant personnel. Establishing open communication channels ensures all stakeholders understand their security responsibilities and can contribute effectively to protective efforts.
Collaboration with external security experts, industry partners, and regulatory bodies provides valuable perspectives that enhance organizational security capabilities. This cooperative approach helps create comprehensive defenses that address risks from multiple angles while benefiting from specialized expertise.